I recently got a Unifi Dream Router as an upgrade from the Unifi Security Gateway.
One of the differences is that the controller is hosted on the router itself, i quite often use the local access as opposed to going via unifi.ui.com. Since this is exposed locally on 443, i wanted to be able to access it without errors regarding invalid SSL certificates.
I found it was quite easy to provide a valid SSL certificate. I already have a wildcard certificate or *.gsellis.com, so I set a hostname in the internal DNS, and then copied over the wildcard cert and key to the UDR:
scp privkey.pem fullchain.pem [email protected]:/tmp/
Then SSH into the UDR using credentials set in the controller, and navigate to /data/unifi-core/config and replace unifi-core.crt with fullchain.pem and unifi-core.key with privkey.pem. Once done you can restart the UI with:
systemctl restart unifi-coreAnd then navigate to the DNS name you set earlier and hopefully see a valid certificate:
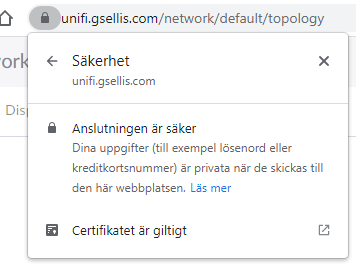
Obviously this will need replacing each time the certificate expires, though i hope to setup a custom configuration in acme.sh to handle this.
4 responses to “Valid SSL certificate on a UDR”
As there is no comment yet: This approach works like a charm, thank you very much for the description. I tried for the first time in September and had to renew now. Everything runs perfect.
Best regards,
Matthias
Is there an option to use custom local domain from hsot file like: unify.local which point to UDR IP, and create cert with LetsEncrypt?
I don’t believe you can get a letsencrypt certificate without a real domain. The verification for issuing the certificate works via either running an agent that letsencrypt talks to (that is reachable via the domain you are verifying), or via updating a public dns entry with a verification token. The only possible solution would be to issue a self signed certificate and trust it on your devices, though that would then be no different really to the default certificate that we’re replacing here.
[…] a follow on from Valid SSL certificate on a UDR, here is an update for the UDM […]