In a recent Beta firmware for various Unifi cloud consoles, Teleport was released.
Under the covers, this appears to be run over wireguard. I have been using Wireguard as VPN for some time, though when I migrated off my USG I have had to run this from a raspberry pi in my network instead.
After installing the beta firmware, I took a look around and found the wg-tools are now installed.
Example config file:
[Interface]
Address = 192.168.100.1/32
ListenPort = 1234
PrivateKey = IPhTq/Mr7iw423t1S6ZV6snsjkzYacD8Mi23ry+hMlU=
[Peer]
PublicKey = y/GNJHLx7DcxFRYLGBbo+i38k2/lmRSM1knUOeGWxH0=
AllowedIPs = 192.168.100.2/32You can generate PrivateKey with :
root@Console:/tmp# wg genkey
IPhTq/Mr7iw423t1S6ZV6snsjkzYacD8Mi23ry+hMlU=and then PublicKey, create a new PrivateKey as above for the first client, and then echo it through wg pubkey. E.g
root@Console:/tmp# wg genkey
CC/Qg+d2vKMJhne6Md8YX2DYIODy/vxTangg46zsJ3A=
root@Console:/tmp# echo CC/Qg+d2vKMJhne6Md8YX2DYIODy/vxTangg46zsJ3A=|wg pubkey
y/GNJHLx7DcxFRYLGBbo+i38k2/lmRSM1knUOeGWxH0=I copied over my config file to my console, and placed in /etc/wireguard as wg1.conf
Enabled the wireguard service for wg1: systemctl enable wg-quick@wg1
Then started the service
root@Console:/tmp# systemctl start wg-quick@wg1You can then check the status
root@Console:/tmp# systemctl start wg-quick@wg1
root@Console:/tmp# wg show wg1
interface: wg1
public key: /BoXnj7ekraL+WQOKUoEH1T4sk8AFkik1TQhK0NK8nI=
private key: (hidden)
listening port: 1234
peer: d8yGQJeuD9NpuZFiMbzagr86bXtG5WuYMBA8mDu6W0c=
allowed ips: 192.168.100.2/32We can see that the interface is up, however nothing connected. To connect we need to configure our client with an equivalent config file. e.g
[Interface]
Address = 192.168.100.2/32
PrivateKey = CC/Qg+d2vKMJhne6Md8YX2DYIODy/vxTangg46zsJ3A=
[Peer]
PublicKey = /BoXnj7ekraL+WQOKUoEH1T4sk8AFkik1TQhK0NK8nI=
AllowedIPs = 192.168.100.1/32
Endpoint = <public IP of console>:1234Where the private key is the private key generated for the client, and the PublicKey is the Private key for server piped through wg pubkey
If you try and connect now, it will likely not work. You need to also create a rule in the firewall for Internet/WAN local allowing inbound UDP on the port you defined in the config file (in my example, port 1234)
In the UI, in Settings -> Firewall & Security, add an entry for Internet Local
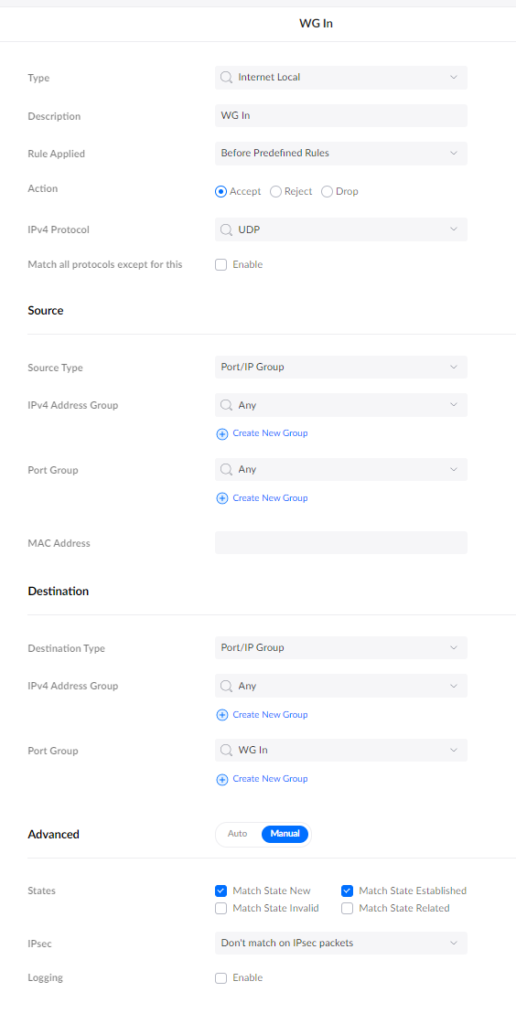
Where the Port Group WG In contains the port you defined in your config file (in my example, 1234).
I have tested restarting the console and the VPN comes back up again, we will see what happens when the next firmware is released.
I expect this should work for all Unifi “all in one” devices (UDM, UDMP, UDR, UDM SE), teleport seems supported on the cloud key too, however I guess that you might need to set up some forwarding from your router to the cloud key to get the wireguard VPN working. Hopefully a UI is added at some point, its a feature thats been requested for some time now.
3 responses to “Wireguard on Unifi”
Thanks for this. I can now connect to my work network using wireguard because of your instructions.
will this ever come to USG 4 pro as it is now on UDM pro.
or do you recommend using a rasberry pi to handle wireguard in the case of having USG 4 pro?
Sorry I missed this.
It is actually possible to install wireguard on the usg, so I assume it could well work on usg pro – take a look here https://github.com/WireGuard/wireguard-vyatta-ubnt
I used this before upgrading to the UDR, it worked well, the configuration was done via the config.gateway.json file. I actually have a draft post here of my configuration,
I’ll have to see if I can finish it and publish it later…Actually here it is: https://www.gsellis.com/configuring-unifi-usg-with-wireguard/